Kaspersky Lab’s newest generation of security software, Kaspersky Internet Security 2018, sports a nifty new feature: support for scanning of encrypted connections, including IMAP/SMTP over SSL between your mail client and your mail servers. While this behavior is mostly desirable, it may occasionally go too far. Kaspersky will intercept your mail connections, inject itself between your mail client and mail server, and use its own certificates to protect the “last mile” of your connectivity. This will cause your mail client to complain about invalid certificates from your mail service providers. The good news is you don’t need to remove the software nor do you need to deactivate scanning of encrypted connections. You can have your cake and eat it too.
Here is how to fix the problem.
Understanding the mail intercept in Kaspersky Internet Security 2018
After installation, Kaspersky Internet Security 2018 intercepts the login credentials which your mail client sends across the network to authenticate for the use of mail services. Having done that, Kaspersky injects its own mail scanning severs between your mail client (such as Postfix) and the Mail Delivery Agent (such as Dovecot) that’s part of your mail server. To its credit, Kaspersky Lab uses its own SSL certificates in order to protect the “last mile” of your connectivity: the communications taking place between your mail client and their network’s mail scanning servers. (Unfortunately, this will do nothing for the security of the connection offered by your mail server to the Kaspersky intercept.)
Now Kaspersky is acting as your mail client towards your mail servers on one hand and as a mail delivery agent towards your mail client (such as Postbox or Thunderbird) on the other hand. As a result, your mail client will keep complaining about certificate mismatches and connection sniffing.
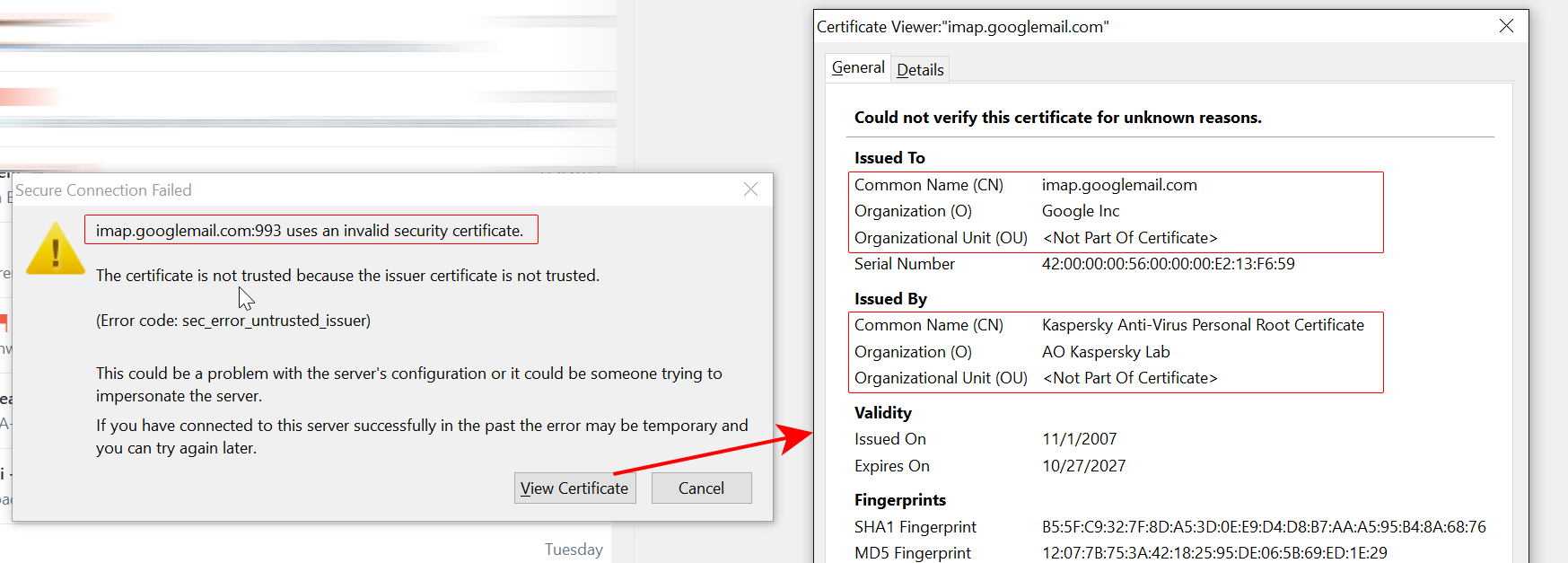
How to fix certificate warnings caused by Kaspersky’s security software
You have basically two options:
- option 1: accept Kaspersky’s SSL certificate as valid by adding the certificate to the list of exceptions in your mail client; Kaspersky will be scanning your mail on their own servers and so you can take advantage of the full scope of functionality of the Kaspersky security software without restrictions
- option 2: deactivate Kaspersky’s surveillance activity by adding your mail host(s) to Kaspersky’s list of exclusions: your mail client will communicate with your mail server without intemediaries so that whatever scanning Kaspersky wants to do on your mail, it has to take place on your local machine
Option 1. is best when handling connections with hosts you do not want to trust (such as ad networks, for example Doubleclick). The specific steps will depend on the mail client of your choice.
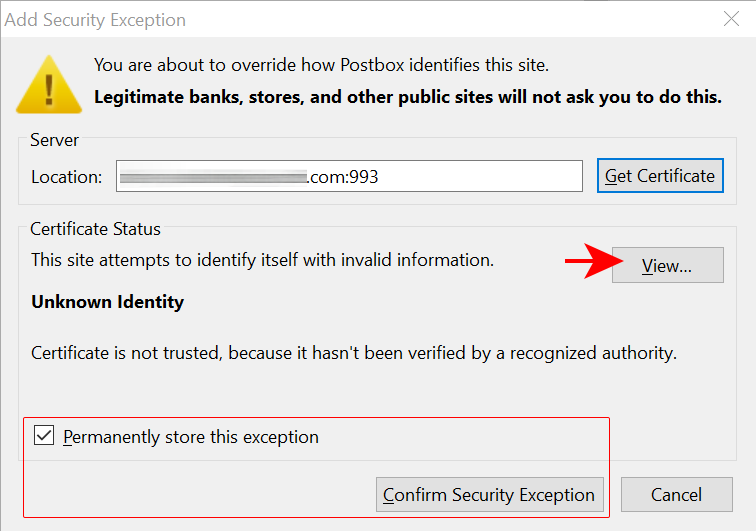
Option 2. is best for communications between your mail client and your own mail providers’ mail server (the so-called MDA, short for Mail Delivery Agent). To set this up, read on.
Deactivate the mail intercept in Kaspersky Internet Security 2018
In order to deactivate the mail intercept in Kaspersky Internet Security, follow the steps below.
Step 1. Edit security Settings in Kaspersky Internet Security 2018
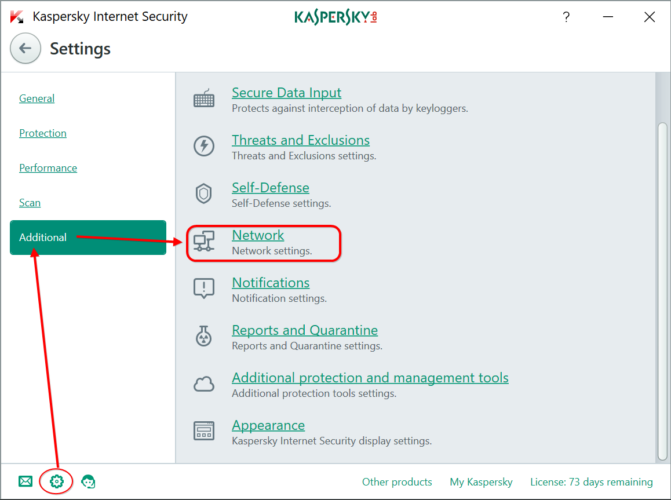
Start Kaspersky Internet Security 2018, click on the Settings icon located at the bottom of the application window.
Step 2. Edit Network settings
In the section Additional of the Settings window, click on Network. Scroll down to the section “Encrypted connections scanning”, activate “Always scan encrypted connections” and click on “Manage exclusions…”.
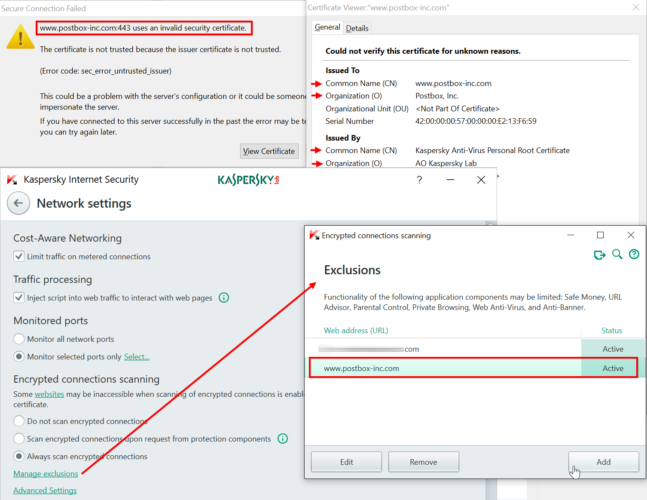
Step 3. Manage exclusions
In the following dialog, click on Add. Enter the host name as it appears in the certificate details section under Common Name. Set the status to “Active” and confirm. Now return to the Network Ports dialog, which is still open. Make sure you keep the option “Monitor all network ports for applications that are vulnerable to network attacks” activated. Confirm by closing the window. Done.
Step 4. Restart your mail client and test the mail connection
Restart your mail client to reset active connections.
Repeat as required for other certificates if you see similar certificate warnings for mail servers that you recognize.

Leave a Reply